Pentest vs Red Team: Key Differences Explained

With the constant rise in cyberattacks mixed with the near-total computerization of today’s businesses, cybersecurity has become a crucial pillar for the proper functioning and health of companies. With the current ever-changing environment, we can no longer develop our security solutions in “Reactive” mode… It’s simply not enough. It is necessary to develop proactive methods to more effectively combat the multiple threats that loom.
An essential solution to integrate into defense methodologies is offensive security. Pentesting and red teaming are two tactics that can be extremely valuable. These two terms are often seen as interchangeable as if they were synonyms. Despite their similar goals, these two techniques have significant differences. This article aims to compare these methods and their selection criteria.
Understanding Red Teaming
Definition And Objectives
The term “Red Teaming” has its origins in the military practices of the United States. To illustrate, here is an excerpt from page 6 of the ‘Red Team Handbook,’ published by the University of Foreign Military and Cultural Studies:
To deepen your understanding of this practice and its military origin, I recommend reading the full ‘Red Team Handbook,’ available here: Red Team Handbook
Over time, Red Teaming practices have developed in an increasingly broad context, reaching the private sector and IT. Today, red teaming in cybersecurity is, in summary, the emulation of an attacker on a network and their facilities.
This technique is used to: - Simulate realistic attack scenarios - Test the reactivity of defense teams (Blue team) - Identify vulnerabilities not detected by standard tests - Improve defense strategies and incident response.
Only a few people are aware of the conduct of a red team operation on their network. We are therefore truly testing the defense capabilities of the blue team. These operations are costly, as they often develop over several weeks, even months. The red team tries to remain stealthy as long as possible. Analyzing the environment, developing exploits, and attacks take time and planning. That’s why Red Teaming is not suitable for every company looking to protect itself.
Application Scenarios
- Large companies with critical infrastructures
- Regulated sectors (Health, Finance)
Exploring Pentesting
Definition And Objectives
Like Red Teaming, penetration tests seek to identify vulnerabilities that may have been missed by standard tests. Pentesting is used to verify the effectiveness of security controls in place. It also aims to validate compliance with security standards and regulations.
Types Of Penetration Tests
- Network test:
- Detection of vulnerabilities in network equipment (routers, switches, firewalls).
- Simulation of Attacks
- Analysis of equipment configurations
- Web application test:
- Security testing of applications (e.g., SQL Injection, XSS (Cross-Site Scripting), CSRF (Client-Side Request Forgery), etc.)
- Code audit
- Tests of authentication and session management
- Physical penetration test:
- Unauthorized access (Attempting access without authorization to assess physical security)
- Employee security tests (Monitoring employees to see if they comply with security protocols)
- Inspection of security devices (Cameras, locks, alarms, etc.)
This list is obviously not exhaustive and only gives you an overview of the different objectives of Pentests.
Comparison Of Approaches
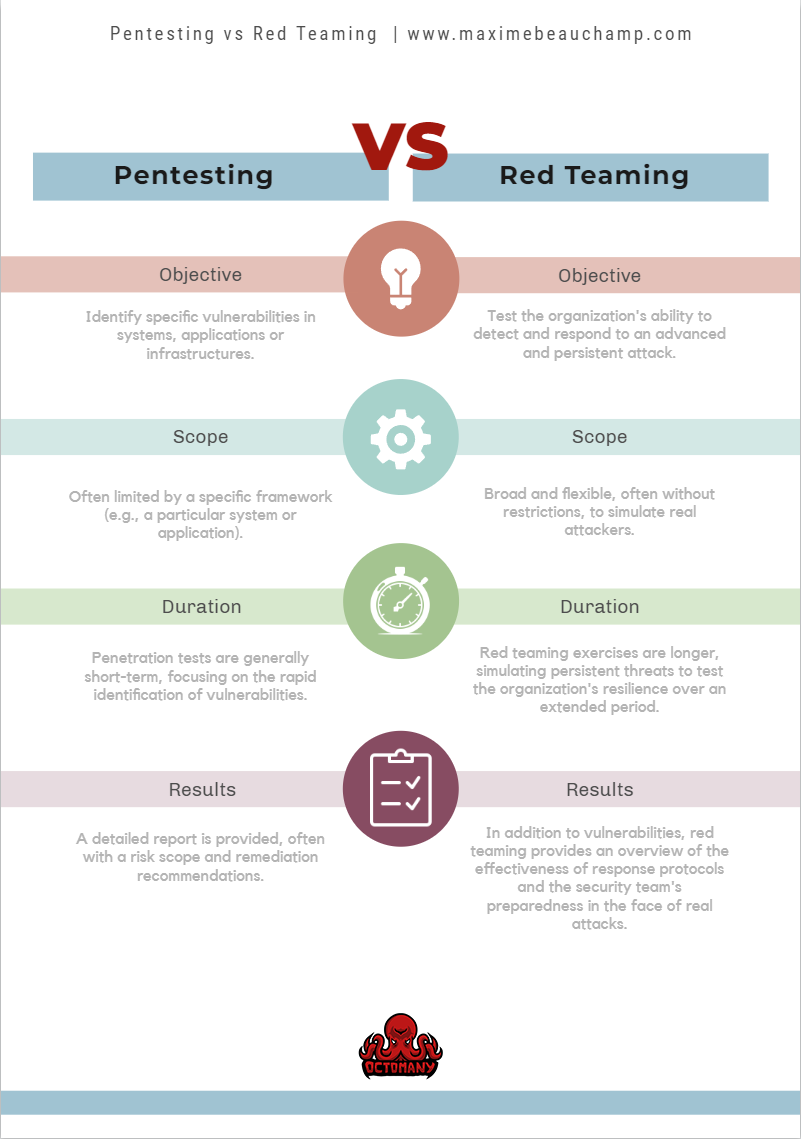
Scale And Scope Of Tests
- Red Teaming: Aims for a complete simulation (All aspects of security with a degree of stealth)
Pentesting: Often targeted at specific applications, with clearly defined objectives.
Level Of Realism
Red Teaming: Realistic attack simulations without prior notice to the blue team, thus testing the full defensive capacity and incident response/reaction.
Pentesting: The realism is more limited for penetration tests since the defensive team is aware of the operation.
Advantages Of Each Method
- Red Teaming:
- Overview: Allows creating a complete portrait of the organization’s security posture. The effectiveness of the blue team can be evaluated in all its aspects.
- Pentesting:
- Rapid correction: The results of penetration tests are often more immediate, thus improving the response time to discovered vulnerabilities.
- Cost: Pentesting is the less costly method between the two options: Tests are shorter and more targeted, so fewer resources are needed to complete them.
- Number of vulnerabilities: Pentesting aims to discover all existing vulnerabilities that could affect the target.
Limitations And Challenges
- Red Teaming:
- High cost: Requires significant resources to simulate realistic scenarios.
- Specialized teams: Requires security experts with the ability to simulate credible attacks
- Pentesting:
- Less suited to complex scenarios: Pentesting may not fully capture the dynamics of a realistic attack.
- Focused vision: More limited scope, thus risking missing some vulnerabilities.
Use Cases For Red Teaming And Pentesting
- When to use Red Teaming:
- Highly secure environments
- Preparation for complex security audits
- When to opt for Pentesting:
- Development of new applications
- After major updates
- Combining both methods:
- Sequential use for complete coverage
- Joint use for a comprehensive security audit
Conclusion
In the world of cybersecurity, staying up-to-date is crucial. With the escalation of cyberattacks, it is evident that reacting to threats is no longer sufficient; we must anticipate and act upstream. Tactics such as Red Teaming and Pentesting are at the heart of this proactive approach. These methods, while similar in their goal of securing, differ enough to be used complementarily rather than interchangeably.
Red Teaming is perfect for those seeking a comprehensive and realistic analysis of their defenses, suitable for large structures with high security stakes. Pentesting, on the other hand, is ideal for quick and precise checks, great for identifying and fixing specific vulnerabilities quickly and efficiently.
Choosing between these two approaches will depend on the specific needs of your organization, available resources, and the type of data to protect. In the end, the important thing is not to settle for a single method. Combining Red Teaming and Pentesting can offer a comprehensive view and robust defense, ready to face the cyber threats of tomorrow. So, keep an open mind, stay proactive, and continue to strengthen your defenses to stay one step ahead of the hackers.
